Security
Firewall
A firewall is an apparatus that is placed in a location in contact with unspecified communication destinations, such as devices for connecting to the Internet, and that blocks unnecessary external communications.
- Static packet filtering
- Static packet filtering enables you to specify the communication type of a packet passing through a network device using the IP address, port number, etc., and pass or block the packet in accordance with preset conditions.
- Dynamic packet filtering
- In dynamic packet filtering, the router automatically determines whether communication is from an already trusted source, such as a terminal on the LAN side, and generates and removes packet filters as necessary.
- IDS - Intrusion Detection System (unauthorized access detection)
- You can use IDS to detect attacks and intrusion from unauthorized packets that use IP, ICMP, UDP, TCP, FTP, SMTP, etc., and discard the packets as necessary.
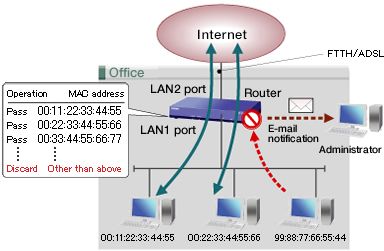
MAC address filtering
You can use MAC address filtering to allow packets to pass or discard them according to their MAC addresses.
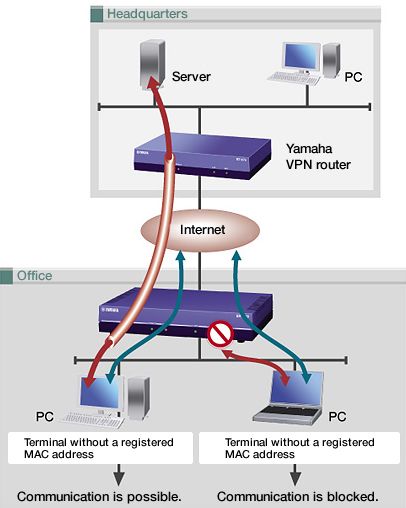
DHCP client authentication
You can use DHCP client authentication to control the networks that terminals can access by distinguishing between terminals on the LAN for which communication with a specific network is permitted and those for which communication is not permitted. DHCP clinet authentication enables you to prevent a terminal brought in from the outside that doesn't have permission from connecting to a network.
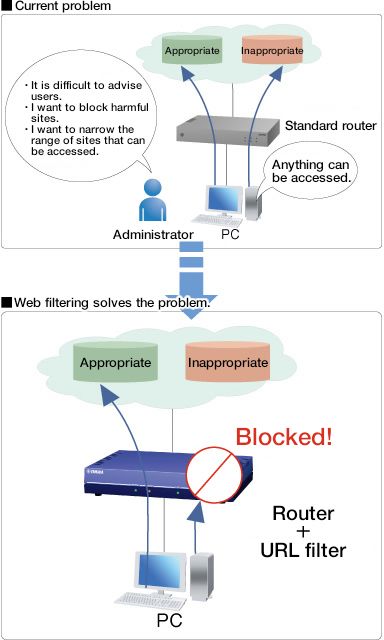
URL filtering
URL filtering enables you to control Web access. When URL filtering is performed using an internal database, the router determines whether to allow a connection to a particular URL based on the URL character string.
P2P detection protection
You can use P2P detection protection to detect and block communications by the filesharing software Winny. This function is compatible with Winny Version 2 & Share Version 1.
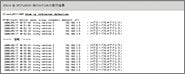
Examples of logs from when Winny filtering is used
Unauthorized access detection history
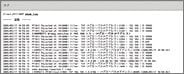
Log contents